A Solo Woman Traveling uses human-written content that contains affiliate links and is a member of Amazon Services LLC. When you make a purchase on a link, we may receive a small commission. This is at no extra cost to you. See Our Affiliate Policy and Advertiser Disclosure for more info.
Planning a trip to Austria and wondering if two days in Salzburg is enough? From my experience, two days can absolutely work for soaking in the charm and seeing the main highlights of this beautiful city—if you plan smartly.
Though the time is a bit tight, I’ve put together the perfect two-day itinerary that covers Salzburg’s top-rated sights.
Whether you choose to follow it to the letter or mix things up to match your travel style, you’re sure to make the most of your time in this stunning Austrian gem.

Is 2 Days REALLY Enough In Salzburg?
Salzburg is small, and with a thought-out itinerary, visiting the city in just two days is enough. My best advice is to arrive early, and have a plan so you don’t waste time.
Keep in mind that surrounding area around Salzburg also has a lot to offer. But, if you were planning on days of excursions you will need a few more than a couple of days in Salzburg.
When I visited, I was on a tight schedule before traveling to Romania. Yet, I managed to get around to nearly everything on my Salzburg bucket list.


Things to Consider When Planning Your Two-Day Itinerary
- When I have only a couple of days in someplace new I stay as central as possible. Does this cost a little more, yes, but you know what they say… Time is money. Don’t try to save a few bucks by staying outside the city center. You would lose valuable time if you stay far away.
- Spend time researching the city and historic sites before arriving to ensure you don’t miss a thing! And also that you want to spend your precious time at that museum, for example. My go-to travel planning tip is always to book a walking tour or bus tour on the first day of the trip.
- Consider the time of year you are visiting. The best time to visit Salzburg is the summer months, but it’s also the most expensive time to visit. I prefer the fall or December to visit Christmas markets.
The Best Time to Visit Salzburg

Salzburg is truly magical no matter what time of year you visit. My personal preference is to travel to Europe in September.
It is far less crowded and the prices are a little bit cheaper. The weather in September is still pretty great.
Another amazing time to visit Salzburg is in December! There are so many things to do in Salzburg in winter.
Austria, in general, has some of the best Christmas Markets!
Getting to Salzburg via Public Transportation
Salzburg is easy to reach from major cities such as Vienna or Munich.
Traveling from Vienna will take approximately take 2 1/2 hours by train, or 2 1/2 by bus. Transit times are similar to Munich.
If you only have a couple of days, try and arrive as early as possible!
The Salzburg transit info can be found by visiting the site for the local bus and trolly. Here you can buy day tickets in advance, saving you time and money.
Everything is digital these days. I would recommend downloading the Transit App by clicking HERE.
Grab the FREE Google Map of Salzburg with the best locations of this post already pre-pinned!!
Day 1: What to See in Salzburg in 2 days
Day 1 Itinerary Overview
Morning: Mirabell Palace & Gardens
Afternoon: Hohensalzburg Fortress & Lunch
Late Afternoon: Old Town Salzburg, Salzburg Cathedral, Residenplatz
Evening: Dinner at St. Peter Stifskulinarium
When creating my own itinerary I had to decide what I was most interested in seeing.
The standout main attractions of Salzburg are Fortress Hohensalzburg, Mozart’s birthplace, and Mirabell Palace.
Morning:
Mirabell Palace
Start your day early with a visit to the Mirabell Palace and Gardens. Take your time strolling through the beautifully landscaped gardens, which were featured in “The Sound of Music”.
Mirabell Gardens are as if taken straight from a romantic novel. Here you will find marble statues, fountains, and grottoes.
TICKETS: get tickets to see a concert at Mirabell Gardens.
Mirabell Palace is one of Salzburg’s most iconic landmarks! You often see it featured on postcards and souvenirs across Austria. It is one of the top things to do in the city of Mozart.
The palace also houses marble halls where you can admire the baroque architecture.
For breakfast, consider stopping by Café Mirabell, located within the palace grounds, offering delightful pastries and coffee.


Afternoon:
Hohensalzburg Fortress
Head to Hohensalzburg Fortress just before lunchtime. You can either walk up to the fortress for a bit of exercise or take the funicular railway for a quick ascent.
Fortress Hohensalzburg is one of the largest and most impressive medieval castles in central Europe!


Have lunch at the Hohensalzburg Fortress Restaurant, where you can enjoy traditional Austrian dishes with a panoramic view of the city.
Spend the rest of your afternoon exploring the fortress. Be sure to check out the medieval chambers, the fortress museum, and the various lookouts for some of the best views over Salzburg and the Bavarian Alps.


If you want to take your experience further, you can dine at the Hohensalzburg castle while enjoying the sounds of the Mozart concert!
The Prettiest Digital Travel Planner
The Notion Travel Planner features 100+ ChatGPT-powered travel prompts, a credit card points tracker, budgeting tools, direct access to 50+ pre-pinned Google Maps from this site, and more—all beautifully organized in one easy-to-use space.
Evening:
Explore Old Town
Descend from the fortress and explore the historic Old Town (Altstadt). Wander through Getreidegasse, famous for its old-world charm and Mozart’s birthplace.


Residenzplatz
The Residenplatz is a magnificent forecourt between the archiepiscopal residences in the heart of Salzburg’s Old City.
It is bordered by the New Residence with its carillon, the Cathedral, the Old Residence, and a continuous row of townhouses.
Salzburg Cathedral
The impressive Salzburg Cathedral of Baroque architecture can be found in the center of the old town! Built between 1614 and 1628 this Roman Catholic church, is one of the most known tourist attractions in Salzburg.
Sound of Music fans might recognize it as it was the backdrop to the famous 1965 film.
One of the best things to do is to climb to the top of the viewing tower where you are rewarded with the most stunning views of the city!
For dinner, enjoy a hearty meal at St. Peter Stiftskulinarium, one of Salzburg’s oldest restaurants, known for its regional specialties.
Cap off the night with a classical music concert at the Salzburg Marionette Theater or the Mozarteum, depending on the schedule.
Organized Walking Tour
Rather not DIY your first day in Salzburg? Consider this 2.5-hour walking tour of Salzburg! It is a great way to knock out the major attractions in Salzburg!
You will start at Mirabell Palace and move on from there to see the Old Town Salzburg (UNESCO world heritage site), and the birthplace of Mozart, and end the tour at Mönchsberg with a panoramic view.
Joining this tour is an especially good tour if you are traveling alone! Make a friend or two on your first day of the trip!
Day 2: What to See in Salzburg in 2 days
Day 2 Itinerary Overview
Morning: Breakfast at Cafe Würfel Zucker, Mozart’s Residence & Salzburg Museum
Afternoon: Hellbrunn Palace
Late Afternoon: Old Town Salzburg, Salzburg Cathedral, St. Sebastian Cemetary
Evening: Hanger 7, and Dinner at Restaurant Ikarus
Morning:
Grab a quick breakfast or a snack at Café Würfel Zucker before your museum visits.
After breakfast head to Mozart’s Residence (Mozart Wohnhaus) to delve into Mozart’s life and work. Plan to spend about an hour to an hour and a half here.
Follow this with a visit to the Salzburg Museum. Since it’s close to Mozart’s Residence, it’s a convenient next stop.
This museum offers insights into Salzburg’s art, history, and traditions. Allocate at least an hour to explore.
TICKETS: Get FREE Admission to Museums & Mozarts House by Purchasing a Salzburg Card!


Late Morning to Early Afternoon:
HELLBRUNN PALACE
Hellbrunner Wasserspiele is known as a true wonder that can still be experienced today although it was built more than 400 years ago. A 17th-century Baroque country estate located just outside the city of Salzburg.
Here you will find Mystic caves, water-driven figures, and treacherous spray wells!
From the city center, you can reach the palace in just 20 minutes on public transit.
Lunch at Café Restaurant Schloss Hellbrunn is still a great idea after exploring the palace.
Afternoon:
Visit St. Sebastian’s Cemetery after lunch for a quieter moment in the day. You won’t need more than an hour here, which allows for a relaxed pace.
Late Afternoon to Evening:
Your last major stop for the day will be Hangar-7. Given that it’s a modern museum with possibly extended opening hours, visiting in the late afternoon or early evening could work well.
Hanger-7 is located at Salzburg Airport. This unique building houses the historical Flying Bulls aircraft and a collection of Formula 1 race cars.
It also has, Restaurant Ikarus, two bars, an outdoor lounge, and one cafe. It’s an event location, and a meeting point for art lovers and bons vivants, too.
You will need to take a bus or taxi from the old town of Salzburg.
Evening:
Consider an easygoing end to the evening with a stroll around the city center or a nightcap at a local bar.
Where to Stay for Two Nights in Salzburg
The Best Boutique Hotels in Salzburg
- Hotel Goldgasse is a special hotel located in Old Town. I stayed here and loved it! Simply creative and cool are the best ways to describe the hotel’s atmosphere.
- Hotel Goldener Hirsch is traditional and exceptional when it comes to the aesthetics of this hotel.
- Arthotel Blaue Gans is a great choice for a boutique modern-style hotel.
Luxury Hotels in Salzburg
The most luxurious hotels can be found in Salzburg. If you are looking to treat yourself to a one-of-a-kind experience, look no further.
- Hotel Sacher Salzburg This hotel is FANCY. Bling, bling, Oprah would stay here fancy.
- Hotel Castle Mönchstein With the word “Castle” in the name, do I really need to say more? This is the kind of hotel that is more of an experience.
- Sheraton Grand Salzburg This hotel is rated as “fabulous” by previous guests. Centrally located, modern, and clean!
Budget Hotels in Salzburg
If a lady is looking for ways to spoil herself in Salzburg but is traveling on a tight budget, here are some tips for you:
Language Spoken in Austria
In Austria, the language is German. It is Austrian German, which has a little bit of a different dialect. The most important words to know are:
- Good Morning – Guten Morgan
- Beer – Bier
- Wine – Wein
- Where is the toliet – Wo ist die toiletten
- Thanks- Danke
Currency
In Austria, you will need to have Euros, and I would suggest you need approximately 100 euros per day for spending money.
Austria is not the cheapest place I have visited, not the most expensive either. Luckily in Salzburg, you can use your credit card in most establishments.
Can Salzburg Just Be a Day Trip?

It would be possible to make a day trip out of Salzburg if you are staying within 2 hours of the city.
But personally, after visiting Salzburg, I would recommend that you try and stay a minimum of 2 full days and nights.
*An optimal stay of 3 nights is ideal for this small city.
Is Salzburg Safe for Visiting Solo?
Oh, yes, Salzburg is very safe! So, for all you solo female travelers looking for safe destinations in Europe, consider Salzburg!
It is one of the safest and best European cities to travel alone as an independent woman! As a frequent solo traveler, safe cities are significant to me.

In general, I don’t think you can go wrong in Europe! I find it especially easy traveling solo in Salzburg even as a beginner!
The Easiest Way I’ve Saved Hundreds on Travel
Solo travel can get expensive! So don’t waste anytime on educating yourself how you can actually stay for FREE by utilitzing credit card points!
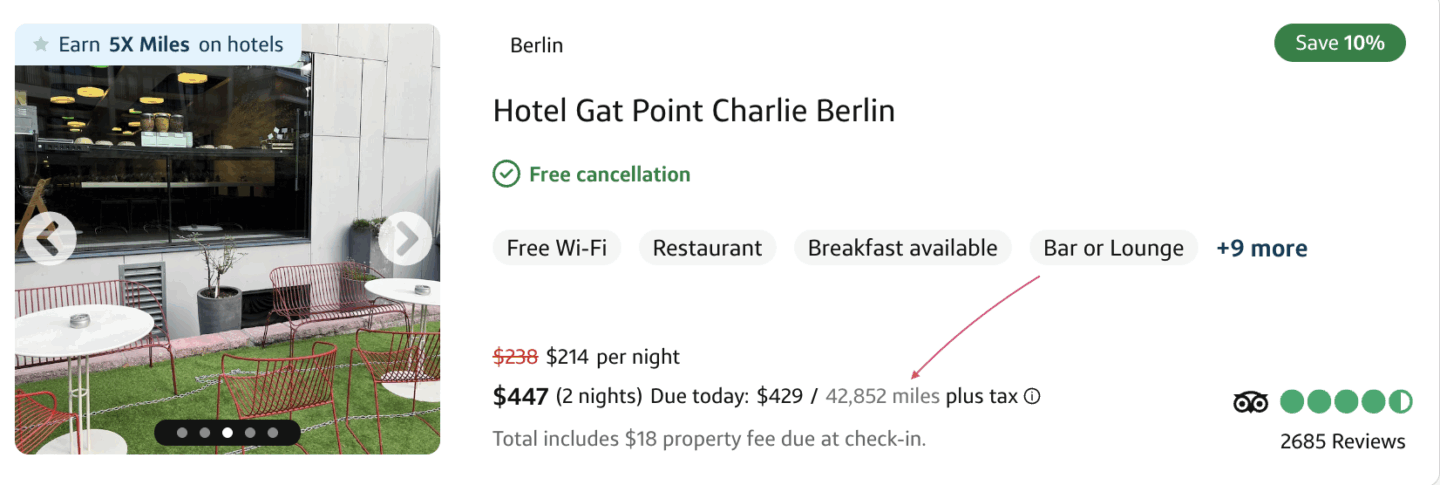
Example: On my recent 2-night stay in Berlin, I only had to pay the hotel tax because I was taking advantage of the points I had from my card.
Not Sure Which Credit Card Might Be Right For You? Check out the new Card Match Tool powered by The Points Guy, and get matched with the best cards for you! *Note may not display all available offers.
Looking for a Solo Female Travel Community?
Are you looking to be part of a tribe of like-minded travelers? As a solo travel expert since 2009, I share my travel hacks and tips inside my exclusive FREE Facebook Group. Join today!
Wrapping Up 2 Days in Salzburg
As the curtain falls on your two-day exploration of Salzburg, you’ll have wandered through the opulent halls of Mirabell Palace, stood atop the city at Hohensalzburg Fortress, traced the footsteps of Mozart, and much more.
In just 48 hours, Salzburg has revealed its treasures, leaving you with a rich collection of sights, sounds, and tastes to cherish.
This itinerary has been more than a simple checklist of attractions; it has been a gateway to the heart of Austrian culture.
Another idea to to head over to Hallstatt for a more serene adventure.
Hallstatt is approx. 2 hours by train from Salzburg. BOOK DAY TRIP TO HALLSTATT
Hallstatt is located on the western shore in Austria’s mountainous Salzkammergut region.
The most recommended way to travel to Hallstatt would be by train.
Pin it for Later!









Great post! I’d love to go to Salzburg one day. I visited Vienna last year and it’s my favorite city I’ve ever visited!
This is such a great post! My dad’s family are from Austria, and when deciding on place to do my student exchange from New Zeland in 2017, Salzburg was on my list, but I ended up choosing the Netherlands! I’m still yet to go to Salzburg! It’s such a beautiful city and these recommendations are so great! Thank you for sharing!
I recently returned from a trip to Salzburg, where I was able to visit beautiful castles and enjoy traditional Austrian cuisine. It was an unforgettable trip and I can’t wait to go back and explore more of this stunning country.