PKCS Definition
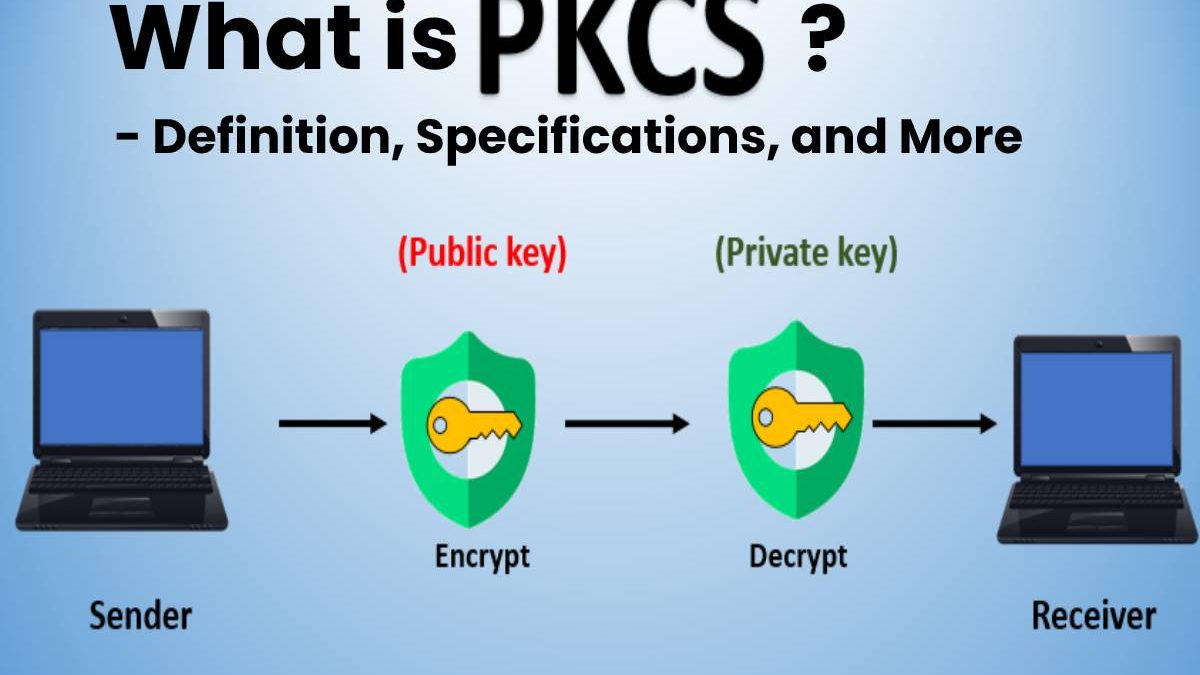
PKCS(Public-Key Cryptography Standards) is a collection of specifications and standards for asymmetric cryptography.
The collection aims to contribute to the spread of asymmetric encryption systems and to advance standardization.
The Public Key Cryptography Standards have incorporated into various standardizations of the IETF and its PKIX working group.
And also, It is the collection of standards and specifications for asymmetric encryption systems.
Also Read: What is a Samsung Knox? – Definition, How Does it Work and More
What are the specifications of PKCS?
- Firstly, The documents aim to contribute to the spread of asymmetric encryption systems based on the public key process and to promote their standardization.
- And also, The specifications are used, for example, for digital signatures and certificates.
- Some of the published documents have incorporated into various standardizations of the IETF and its PKIX working group.
What are the Public Keys of [PKCS]?
Below is a brief overview of the 15 different areas of the Public-Key Cryptography Standards and their respective contents:
- RSA procedure – Public-key procedure based on the RSA algorithm – mechanisms for signing and encrypting the data.
- Missing – was merged with PKCS 1 and withdrawn.
- The standard for the Diffie-Hellman key exchange is a description of the necessary data exchange formats.
- Missing – was merged with PKCS 1 and withdrawn.
- Recommendations for implementing password-based encryption is deriving encryption from the password.
- Extended-Certificate Syntax Standard is a Description of the syntax for extended certificates and their attributes.
- Cryptographic Message Syntax (CMS) – cryptographic formats for encrypted and
signed messages (used, among other things, as a syntax for S / MIME) - Private-Key Information Syntax is Standard for describing the syntax of a private key and its attributes.
- The standard is the description of attributes of extended certificates, such as those used in PKCS standards 7, 8, 10, 12 or 15.
- Certification Request Syntax – And also, the standard for describing the syntax of certification requests for public keys.
- Cryptographic Token Interface – And also, the standard for specifying an interface for hardware modules for the transmission of cryptographic information (Cryptoki).
- Personal Information Exchange Syntax – Standard for describing the syntax of a portable format for private keys and certificates.
- The standard is the description of the Elliptic Curve Cryptosystem (ECC) and its parameters.
- Pseudo-Random Number Generation (PRNG) Standard – is still under development or partially discontinued.
- Cryptographic Token Information Format -And also, the standard for describing the format of cryptographic tokens.
Also Read: What is a User Profile? – Definition, Types, and More
Kamran Sharief
Related posts
Sidebar
Recent Posts
The Best Forex Brokers for Beginners
Since COVID-19 first popped up, interest in the forex market has increased dramatically. Knowing how to get involved with minimal…
Maximizing Success: The Symbiosis of Dedicated Software Development Teams and Product Design Services
The Symbiosis of Dedicated Software Development Teams and Product Design Services In the rapidly evolving landscape of technology, businesses aiming…